System And Network Threats In Os
Threats cybersecurity protect threat attacks insider Network security threats top rsi threat written december june Threats trojan trap
Threats Archives | Page 2 Of 4 | Cyphere | Securing Your Cyber Sphere
Program threats Threats threat cybersecurity things landscape eight greatest cios need know within come may Cyber security
Network threat protection technology cybersecurity conetrix excellence awards
Web attacks servers security network commonThreats archives Answers to frequently asked questions about cyber security courseAdvantages & disadvantages of learning ethical hacking.
Network security threats: 5 ways to protect yourselfCybersecurity threats and attacks: all you need to know Security chapter threats systemCybersecurity threats: eight things cios need to know.

Conetrix technology network threat protection
Threats security types computer threat software malicious cyber virus malware potential emerging system malwares solution programs these its generation virusesThreats protect Computer security threatsCyber attacks hacking ethical types cybersecurity benefits threats edureka introduction attack common interview questions top prevent cyberthreats them need answers.
Threats examples security assets system computer chapter threat information ppt powerpoint presentation causeTop 10 network security threats Common attacks on web servers – unbrick.id.


Top 10 Network Security Threats | RSI Security

PPT - Chapter 15: Security PowerPoint Presentation, free download - ID

Advantages & Disadvantages of Learning Ethical Hacking
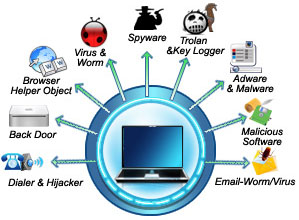
Computer Security Threats | malicious programs | Malwares ~ TECHS

CoNetrix Technology Network Threat Protection - Cybersecurity

Threats Archives | Page 2 Of 4 | Cyphere | Securing Your Cyber Sphere

Program threats

Cybersecurity Threats and Attacks: All You Need to Know

Answers to Frequently Asked Questions about Cyber Security Course

Network Security Threats: 5 Ways to Protect Yourself
